The Big Hacks of 2013
2013 has been quite the year for high profile hacks, with hundreds of millions of accounts compromised across a whole range of disparate services.
Here’s our roundup of the big hacks of 2013 and the lessons that can be learned to stay secure in 2014.
Adobe and the fallout
 By far the biggest hack of 2013 happened to Adobe, with customer IDs and passwords stolen on an unprecedented scale. Adobe initially reported that 38 million accounts were affected, but this number rose to 150 million as the true extent of the breach became known.
By far the biggest hack of 2013 happened to Adobe, with customer IDs and passwords stolen on an unprecedented scale. Adobe initially reported that 38 million accounts were affected, but this number rose to 150 million as the true extent of the breach became known.
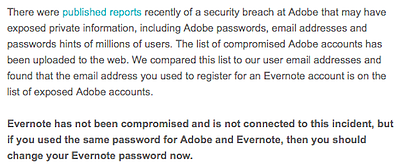
The huge scale of the Adobe hack resulted in security breaches far beyond Adobe itself. Because so many people continue to use the same password across different accounts, when the Adobe credentials were stolen and then posted online, it led to users being compromised on other services that weren’t themselves hacked. Evernote called Adobe out and blamed them for its users being compromised.
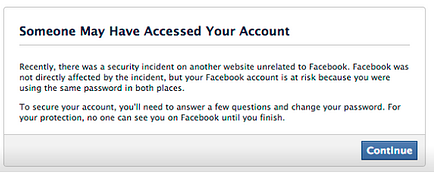
Facebook also blamed Adobe, albeit without naming them - here’s what they told their users.
With so many people mirroring their passwords across different services, it's no surprise that the consequences of the Adobe were so catastrophic.
On Target
 The most-recent high-profile hack happened in December, when discount retailer Target were breached leading to 40 million customers' details being stolen, including their names, credit & debit card numbers, expiration dates and CVVs. The stolen information allowed hackers to clone customer bank cards.
The most-recent high-profile hack happened in December, when discount retailer Target were breached leading to 40 million customers' details being stolen, including their names, credit & debit card numbers, expiration dates and CVVs. The stolen information allowed hackers to clone customer bank cards.
In a bid to repair the massive reputational damage, Target offered customers free credit monitoring services and a 10% store-wide discount for the weekend following the hack – comforting!
If you do, or did, have an account with Target, be sure to check your debit/credit card statements for any unusual activity.
BBC, Associated Press and New York Times
 The Syrian Electronic Army were on a bit of a march in 2013, hacking some high-profile news agency accounts. The BBC and AP had their Twitter accounts compromised, while the New York Times had their website hacked. While it was hugely embarrassing for the organizations, it's perhaps the wake up call they needed to increase their vigilance when it comes to managing employee access to passwords and educating their workforce on phishing attacks.
The Syrian Electronic Army were on a bit of a march in 2013, hacking some high-profile news agency accounts. The BBC and AP had their Twitter accounts compromised, while the New York Times had their website hacked. While it was hugely embarrassing for the organizations, it's perhaps the wake up call they needed to increase their vigilance when it comes to managing employee access to passwords and educating their workforce on phishing attacks.
Vbulletin
One of the most popular forum software providers was breached in 2013 with hackers compromising an insecure system that was used for testing vBulletin mobile applications. The result was hundreds of thousands of Vbulletin users' details stolen, including customer IDs and encrypted passwords .
The hacking group 'Inj3ct0r Team' claimed to have discovered a "0-day exploit" for vBulletin's forum software versions 4.x.x and 5.o.x and used it to hack the hugely popular MacRumors.com website, stealing 860,000 usernames, email addresses and passwords.
MongoHQ & Buffer
MongoHQ was hacked in November due to its own poor password policies - an employee had been using the same password for a personal account and their business MongoHQ account. When the employee's personal account was compromised, the hackers were then able to gain access to the employer's accounts that had been protected using the same password. Unfortunately for Buffer - who used MongoHQ to manage their database - they were compromised once the hackers had gained access to MongoHQ. The hack was a huge embarrassment to Buffer, with the hackers spamming content to Buffer users’ social media accounts.
PHP
In October, owners of the open-source PHP programming language locked down the official php.net website after discovering malicious code had been installed on their site. Hackers injected a malicious iFrame into the website which then installed malware onto visitors' computers. Visitors to the website who did not have anti-virus software install on their devices would have been at most risk. Eventually php.net moved their site to new servers.
Github
 Github's servers were not themselves broken into. Instead, individual Github user accounts protected by weak passwords were targeted and broken into by hackers. Hackers used 40,000 different IP to bypass brute force protection scripts in place on Github, allowing them to try lists of common passwords to access the accounts. Github reset accounts with easily guessed passwords.
Github's servers were not themselves broken into. Instead, individual Github user accounts protected by weak passwords were targeted and broken into by hackers. Hackers used 40,000 different IP to bypass brute force protection scripts in place on Github, allowing them to try lists of common passwords to access the accounts. Github reset accounts with easily guessed passwords.
Vodafone
In September, Vodafone in Germany owned up to having suffered a hacking incident which led to 2 million of its customers’ details being stolen. The sensitive information included customer name, address, date of birth, gender, bank sort code and bank account number.
Facebook, Yahoo, Google & Twitter
 More than 2 million login credntials for a multitude of web services were posted online in December. Of the 2 million, there were 318,121 for Facebook, 59,549 for Yahoo, and 54,437 for Google, and 21,708 for Twitter. Credentials including e-mail addresses, FTP accounts, remote desktops, and secure shells were also found amongst the list.
More than 2 million login credntials for a multitude of web services were posted online in December. Of the 2 million, there were 318,121 for Facebook, 59,549 for Yahoo, and 54,437 for Google, and 21,708 for Twitter. Credentials including e-mail addresses, FTP accounts, remote desktops, and secure shells were also found amongst the list.
It's believed that the login details were obtained from computers infected with malware which logged key strokes as the users logged into their individual or business systems.
What lessons can be learned?
There are some things you can’t affect. For example, unless you’re the Adobe security team reading this, there’s nothing you could do as an individual or company to prevent Adobe being hacked.
What you can do though is mitigate the risk and take steps to ensure that when a company like Adobe is hacked, you and your company are either not affected at all, or at worst, your exposure is isolated.
So, what can you do to mitigate the risk for you and your company?
1. Make your passwords strong - at least 14 characters
2. Don't use the same password more than once
Following these 2 pieces of advice will significantly improve you and your business's security. Long passwords are difficult to crack, so even when Adobe are hacked and your encrypted/hashed password is stolen, it's extremely difficult for the hacker to crack it.
There is plenty of bad advice out there that should be ignored, such as make your password at least 8 characters, and change your passwords regularly. 8 characters is not enough anymore to protect your information, and changing your password regularly is pointless if you're replacing weak passwords with other weak passwords.
If you want to check your current passwords to see just how strong they are, and how long it would take to crack them try out our Password Strength Checker below:
Check out how strong your business passwords are!
 If any of your passwords are weak, you should change them immediately. If your passwords are strong, known only to you, and not used for multiple services, then there's no need to change them. It’s better to have strong password that you don’t change, than to keep changing passwords every few weeks to a serious of weak ones. my1login allows you to use super-strong unique passwords for all your different accounts, and be able to access them with just one set of strong credentials. Client-side encryption means that the data that's stored by my1login is useless in the hands of hackers - it's impossible to decrypt the data without the key, which only you know. my1login has not visiblity of your key, so even we cannot see your passwords!
If any of your passwords are weak, you should change them immediately. If your passwords are strong, known only to you, and not used for multiple services, then there's no need to change them. It’s better to have strong password that you don’t change, than to keep changing passwords every few weeks to a serious of weak ones. my1login allows you to use super-strong unique passwords for all your different accounts, and be able to access them with just one set of strong credentials. Client-side encryption means that the data that's stored by my1login is useless in the hands of hackers - it's impossible to decrypt the data without the key, which only you know. my1login has not visiblity of your key, so even we cannot see your passwords!
What can you expect from 2014?
More of the same hacks and most probably a lot more. The software, hardware and techniques available to hackers today are increasingly sophisticated and easy to deploy. Couple this with the fact that individuals and employees alike continue to make themselves and their businesses an easy target, and it's recipe for the continuing trend.
If you'd like to see how my1login can improve your business's online security and help protect you against hacks in 2014 try out the my1login password manager for free, or leave your email address and we'll send you an information pack.
Related Articles
My1Login named Winner at the 2021 Cloud Excellence Awards
My1Login is delighted to announce that it has been named the Cloud Security Product of the Year for Identity, Access and Authentication at the 2021 Cloud...Why Phishing is so Effective at Stealing Corporate Data
Phishing is not a new phenomenon, but it continues to grow at a rapid pace and remains the most common form of cyberattack. According to Cisco, 86% of organisations...Identity and Access Management for Web, Mobile and Windows Desktop Applications
Identity and Access Management for Web, Mobile and Windows Desktop Applications










-
© My1Login 2007 - 2024
- Terms & Conditions
- Anti-Slavery Policy
- Back to the top ↑